This section will cover ways to attack email services.
Table of Contents
- Overview
- Enumeration
- Identifying Mail Servers
- Nmap
- Authentication
- Cloud Enumeration
- Connection
- POP3
- IMAP4
- Exploitation
- Password Attacks
- Open Relay
Overview
A mail server (also known as an email server) is a server that handles and deliver email over a network. A mail server can receive emails from a client device and them them to other mail servers or deliver to client devices.
Simple Mail Transfer Protocol (SMTP) is the a protocol used to transfer mail from a client to a server or to other servers.
When a client downloads an email that is sent to them, the application used will connect to a server using Post Office Protocol 3 (POP3) or Internet Message Access Protocol 4 (IMAP4).
By default, POP3 clients remove downloaded messages from the email server. This makes it difficult to access emails on multiple devices downloaded messages as the emails are stored on a local device. However, POP3 can be configured to keep downloaded copies of emails on the server.
Clients that uses IMAP4 do not remove downloaded messages from the email server. This makes it easy to access it on multiple device.
The below image is an rough overview of the process where a client is sending another client an email.
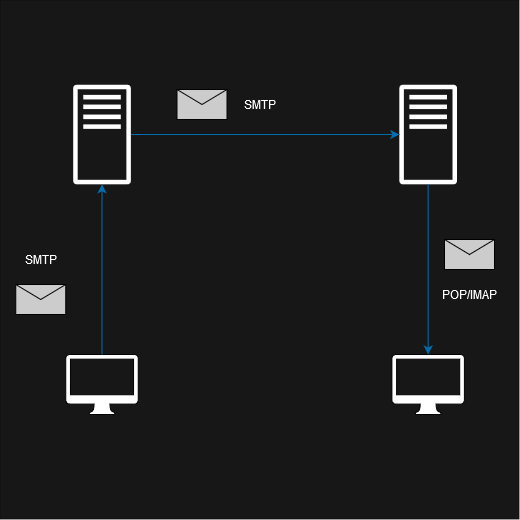
Clients can use SMTP to transfer emails to the server and servers can use SMTP to send mail to each other. The recipient can then use POP3 or IMAP4 to download the email from the server to be read.
Enumeration
There are several tools and methods that can be used to enumerate email services.
This section will cover the following:
- Identifying Mail Servers
- Nmap
- Authentication
- Cloud Enumeration
Identifying Mail Servers
we can use tools such as host or dig to query MX and A records to identify email servers.
Host:
host -t MX <domain>
host -t A <domain>
DIG:
dig mx <domain>
dig A <domain>
Nmap
We can use Nmap and the following command to enumerate specified ports to identify the email client and server used.
nmap -sV -Pn -sC -p 25,110,143,465,587,993,995 <Target IP>
Command breakdown:
-sV- Scan the version of each service.-Pn- Disable ping scan.-sC- Use default NSE scripts.-p 25,110,143,465,587,993,995- Specify the ports to scan.<Target IP>- Specify the target IP address.
The following ports can be enumerated:
| Port | Service |
|---|---|
| TCP/25 | SMTP unencrypted |
| TCP/110 | POP3 unencrypted |
| TCP/143 | IMAP4 unencrypted |
| TCP/465 | SMTP encrypted |
| TCP/587 | SMTP encrypted/STARTTLS |
| TCP/993 | IMAP4 encrypted |
| TCP/995 | POP3 encrypted |
Authentication
We can use VRFY, EXPN, and RCPT TO to enumerate a SMTP server for valid usernames. Once valid usernames are discovered, we can proceed to perform various attacks on the server.
To connect to a server, we can use telnet or nc.
telnet <Target IP> <port>
nc <Target IP> <port>
Once connected, we will need to send a HELO or EHLO with the FQDN name of the email server.
HELO <FQDN>
EHLO mail.mycorp.lan
The below table will list the commands and their description.
| Command | Description |
|---|---|
| VRFY | This command instructs the receiving SMTP server to check the validity of the specified email username. The server will respond if the user exists or not. This can be disabled. |
| EXPN | This command when used with a distribution list with all users on that list. |
| RCPT TO | This command identifies the recipient of the email message. It can be repeated multiple times for a given message to deliver a single message to multiple recipients. |
VRFY:
VRFY <username>
EXPN:
EXPN <list>
EXPN support-team
RCPT TO:
RCPT TO:<username>
We can also use POP3 to enumerate for users depending on the service implementation. An example will be using the USER command followed by the username. If the server responds OK, this indicates that the user exists on the server.
USER <username>
To automate this process, we can use a tool called smtp-user-enum. We can specify the -M switch alongside the command to use. We can also specify the -U switch with a file containing a list of usernames to enumerate.
smtp-user-enum -M <command> -U <username wordlist> -D <domain> -t <Target IP>
Command breakdown:
-M <command>- Specify the email command to use to enumerate.-U <username wordlist>- Specify the username wordlist to use for enumeration.-D <domain>- Specify the domain to enumerate.-t <Target IP>- Specify the target mail server IP address.
An example:
smtp-user-enum -M RCPT -U usernames.txt -D mycorp.lan -t 10.42.0.222
Cloud Enumeration
If the target is using providers such as Office 365 from Microsoft, we can use a tool called O365spray to enumerate the target.
It can be downloaded from GitHub using the link https://github.com/0xZDH/o365spray.
To start, validate if the target is using Office 365 using the following command.
python3 o365spray.py --validate --domain <domain>
Once validated, we can specify a username wordlist to use for enumeration.
python3 o365spray.py --enum -U <username wordlist> --domain <domain>
Once we have the required information, we can perform various attacks on the server.
Connection
We can interact with an email server using POP3 or IMAP4. To connect to a server using either protocol, we can use telnet or netcat.
telnet <Target IP> <port>
nc <Target IP> <port>
POP3
Once connected, we can login using the USER and PASS command with the email address and password respectively.
USER myuser@corp.lan
PASS password123
Once authenticated, we can use commands such as LIST to list unread emails and RETR <id> to read the selected email.
The below table will list some common commands that can be used with POP3.
| Command | Description |
|---|---|
| USER username | Identify the user. |
| PASS password | Authenticate the user with its password. |
| STAT | Requests the number of saved emails on the server. |
| LIST | Requests for the number and size of all emails. |
| RETR id | Requests the server to deliver the requested email by ID. |
| DELE id | Requests the server to delete the requested email by ID. |
| CAPA | Requests the server to display the server capabilities. |
| RSET | Requests the server to reset the transmitted information. |
| QUIT | Closes the connection with the server. |
IMAP4
Once connected, we will can login using the LOGIN command. Note that we will need to add a tag such as a <command> to run the command. The tag name can be anything.
a LOGIN <username> <password>
Once logged in, we can use the SEARCH ALL command to list all emails and FETCH to read an email. The below table will list some common commands that can be used with IMAP.
| Command | Description |
|---|---|
| LOGIN username password | User login. |
| LIST "" * | List all directories. |
| CREATE "BOX_Name" | Create a mailbox with a specific name. |
| DELETE "BOX_Name" | Deletes a mailbox. |
| RENAME "BOX_Old_Name" "BOX_New_Name" | Renames a mailbox. |
| LSUB "" * | Returns a subnet of names from the set of names that the user has declared as active or subscribed. |
| SELECT INBOX | Selects a mailbox so that messages in the mailbox can be accessed. |
| SEARCH ALL | Search for emails. |
| UNSELECT INBOX | Exits the selected mailbox. |
| CLOSE | Removes all messages with the "Deleted" flag set. |
FETCH <ID> all | Retrieves data associated with a message in the mailbox. |
| FETCH 1:1 (BODY[TEXT]) | Fetches the first email message. |
| FETCH 1:1 BODY[HEADER] | Retrieves the header of the first email in the selected mailbox. |
| LOGOUT | Close the connection with the IMAP server. |
Exploitation
There are various attacks that we can perform once we have obtained the required information.
This section will cover the following:
- Password Attacks
- Open Relay
Password Attacks
We can use tools such as Hydra and O365 Spray to perform password spraying or brute force attacks against email services such as SMTP, POP3, or IMAP4. The following example will be using Hydra and O365 Spray to perform a password spraying attack.
hydra -L <username wordlist> -p '<password>' -f <Target IP> <protocol>
Command breakdown:
-L <username wordlist>- Specify the username wordlist to use.-p '<password>'- Specify the password to use.-f <Target IP>- Specify the target IP address.<protocol>- Specify the protocol to attack.
python3 o365spray.py --spray -U <username wordlist> -p '<password>' --count 1 --lockout 1 --domain <domain>
Command breakdown:
--spray- Perform a password spray attack.-U <username wordlist>- Specify the username wordlist to use.-p '<password>'- Specify the password to use.--count 1- Specify how many attempts should be done before moving onto the next user.--lockout 1- Specify the account lockout threshold.--domain <domain>- Specify the target domain.
Open Relay
An open relay is a SMTP server which is improperly configured and allows an unauthenticated email relay.
Email servers that are accidentally or intentionally configured as open relays allow mail from any source to be transparently re-routed through the open relay server. This behaviour masks the source of the messages and make it look like the email originated from the open relay server.
This can be abused for phishing attacks by sending emails as non-existing users or spoofing an email. To identify an open relay server, we can use Nmap and the smtp-open-relay NSE script.
nmap -Pn -p 25 --script smtp-open-relay <Target IP>
Command breakdown:
-Pn- Disable ping scan.-p 25- Specify the target port.--script smtp-open-relay- Specify the NSE script to use.<Target IP>- Specify the target IP address.
To connect and send an email using an open relay, we can use swaks and the following command.
swaks --from <Sender email> --to <Recipient email> --header '<header content>' --body '<body content>' --server <Open Relay Server IP>
Command breakdown:
--from <Sender email>- Specify the sender's email address.--to <Recipient email>- Specify the recipient's email address.--header '<header content>'- Specify the header contents.--body '<body contents>'- Specify the body contents.--server <Open Relay Server IP>- Specify the IP address of the open relay server.
An example:
swaks --from notifications@mycorp.lan --to employees@mycorp.lan --header 'Subject: Org Notification' --body 'This is an email sent from an open relay.' --server 10.42.0.220